Docker has revolutionized the world of software development, packaging, and deployment. The platform has enabled developers to create portable and consistent environments for their applications, making it easier to move code from one environment to another. Docker has also improved collaboration among developers and operations teams, as it enables everyone to work in the same […]
Read more →Category: DevOps
MLOps Best Practices: Building Production Machine Learning Pipelines That Scale
Master MLOps practices for production machine learning systems. Learn data versioning, experiment tracking with MLflow, CI/CD for ML, model registry governance, and monitoring strategies for AWS, Azure, and GCP.
Read more →The Rise of GitOps: Automating Deployment and Improving Reliability
GitOps is a relatively new approach to software delivery that has been gaining popularity in recent years. It is a set of practices for managing and deploying infrastructure and applications using Git as the single source of truth. In this blog post, we will explore the concept of GitOps, its key benefits, and some examples […]
Read more →GitOps with a comparison between Flux and ArgoCD and which one is better for use in Azure AKS
GitOps has emerged as a powerful paradigm for managing Kubernetes clusters and deploying applications. Two popular tools for implementing GitOps in Kubernetes are Flux and ArgoCD. Both tools have similar functionalities, but they differ in terms of their architecture, ease of use, and integration with cloud platforms like Azure AKS. In this blog, we will […]
Read more →An Introduction to DevSecOps: Unlocking Success with Real-World Examples
Introduction In today’s fast-paced world, the need for rapid and secure software development has never been more crucial. As organizations strive to meet these demands, the DevSecOps approach has emerged as a powerful solution that integrates security practices into the DevOps process. By combining development, security, and operations, DevSecOps enables teams to create high-quality, secure […]
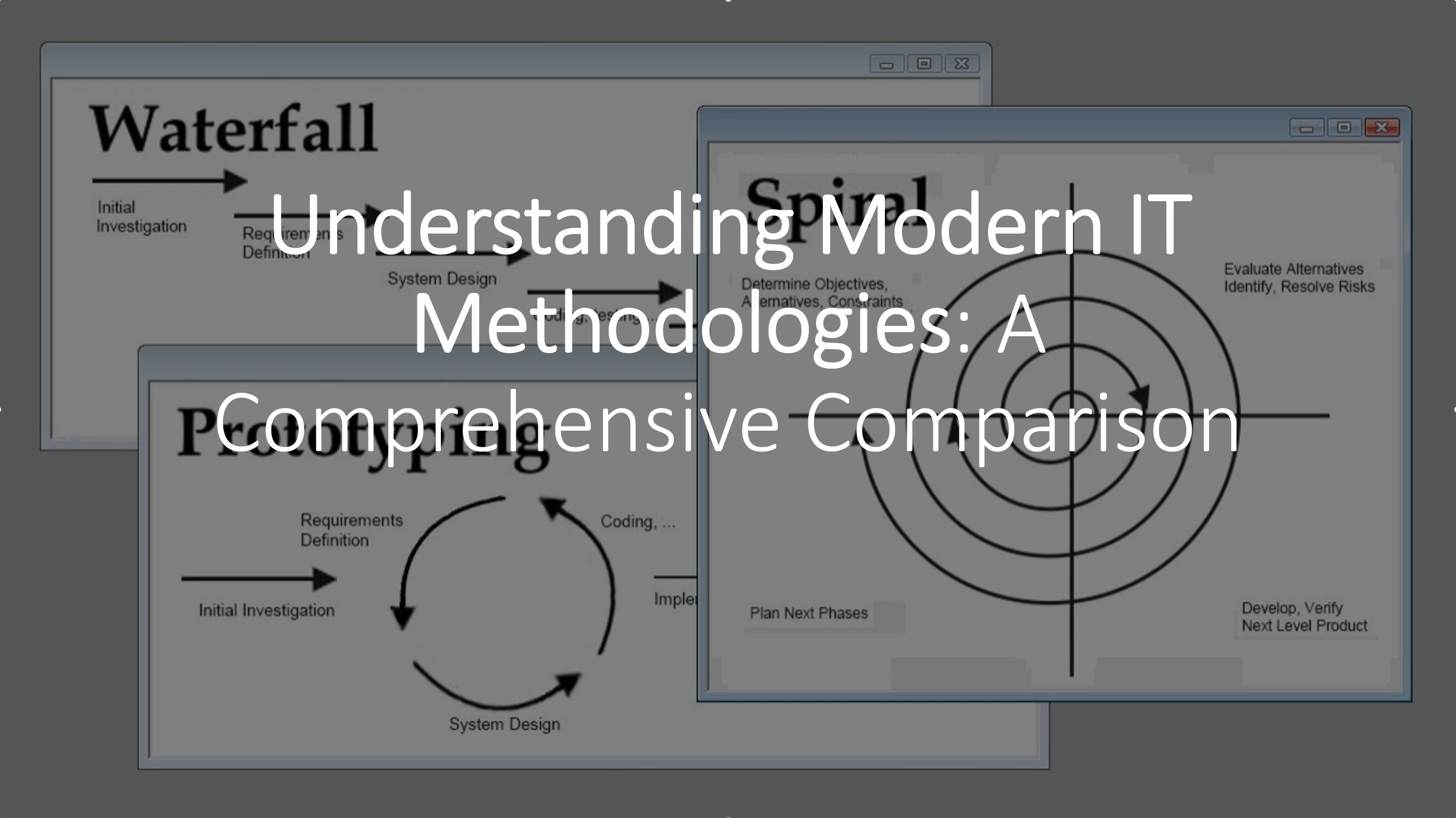
Read more →Understanding Modern IT Methodologies: A Comprehensive Comparison
After two decades of building and operating enterprise systems, I’ve watched the IT operations landscape transform dramatically. What started as siloed development and operations teams has evolved into a rich ecosystem of methodologies, each addressing specific organizational challenges. In this comprehensive guide, I’ll share my perspective on four dominant approaches: DevOps, DevSecOps, Site Reliability Engineering […]
Read more →