Executive Summary
Part 2 of 2: Implementation & Best Practices
🏥
HEALTHCARE INTEROPERABILITY SERIES
This article is part of a comprehensive series on healthcare data standards and interoperability.
- HL7 v2: The Messaging Standard That Powers Healthcare IT
- Building GDPR-Compliant FHIR APIs: A European Healthcare …
- EMR Modernization: Migrating from Legacy HL7 v2 to FHIR
- HL7 v3: Understanding RIM and Why v3 Failed to Replace v2
- FHIR Subscriptions: Building Real-Time Event-Driven Healt…
- ePrescribing in EU and Ireland: FHIR-Based Electronic Pre…
- FHIR Integration Best Practices: Lessons from Production
- FHIR API Security Part 1: Foundation & Authentication
- FHIR API Security Part 2: Implementation & Best Prac… (this article)
- Real-Time Healthcare Data Pipelines: Kafka + FHIR for Cli…
- Building Interoperable Healthcare Data Systems for AI: A …
- Case Study: Building a Modern FHIR Patient Timeline Explo…
DPoP Implementation (.NET)
What is DPoP?
Demonstrating Proof-of-Possession (RFC 9449) binds access tokens to a cryptographic key pair:- Client generates RSA key pair
- Client creates signed JWT proof
- Server binds token to public key
- Each request requires fresh proof
- Stolen tokens are useless
- Token binding prevents theft
- Replay protection with unique jti
- No shared secrets transmitted
- Man-in-the-middle prevention
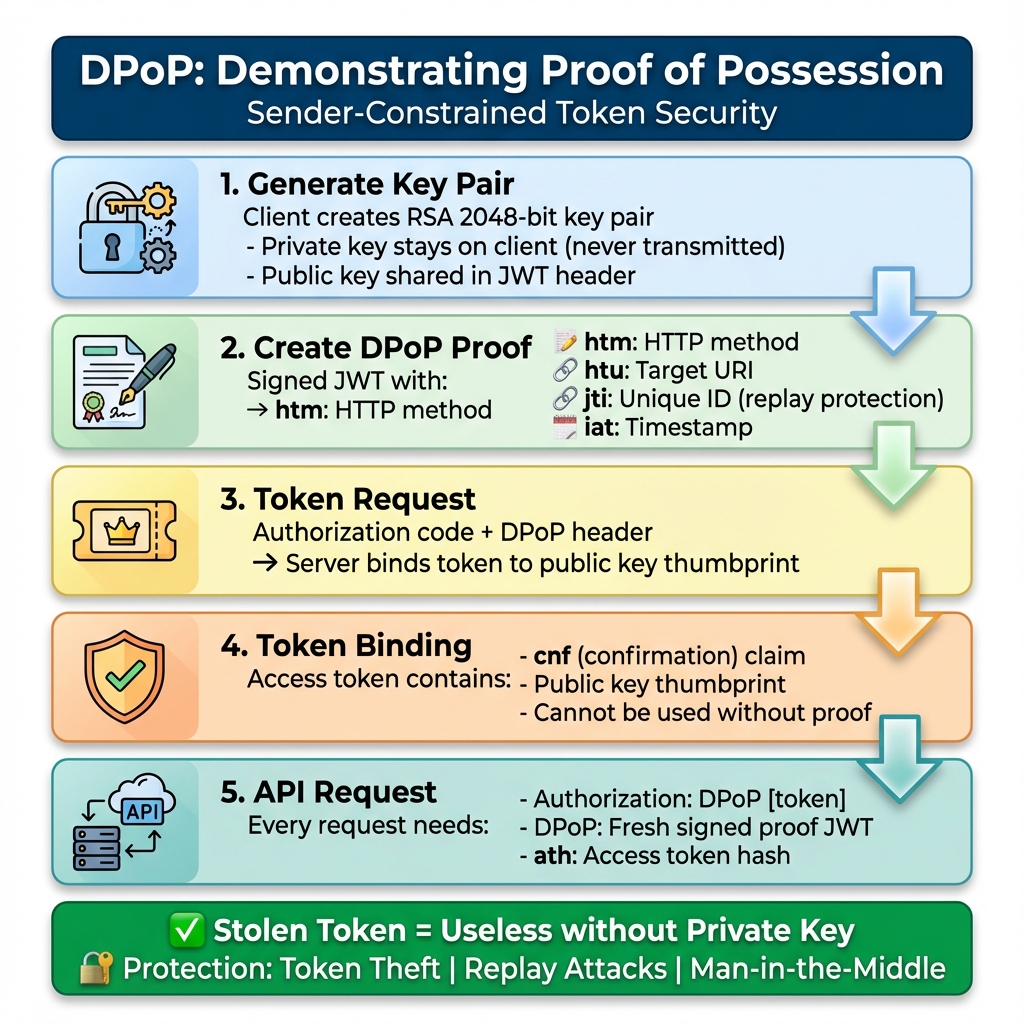
My First DPoP Implementation (And What I Learned)
I’ll be honest: the first time I implemented DPoP, I thought it was overkill. "Why add this complexity when OAuth 2.0 works fine?" I asked my security lead. Then we did a penetration test. The tester intercepted a bearer token from network traffic (despite TLS—long story involving a compromised client) and used it to access patient data for 45 minutes before our monitoring caught it. That was my wake-up call. With DPoP, that stolen token would have been useless. The attacker didn’t have the private key, so they couldn’t generate valid proofs. The code below is what I wish I had when I started. It’s production-tested, handles edge cases, and includes the error handling I learned the hard way.Before We Dive In
I could recollect a production had a bug that caused token validation to fail every Sunday at 2 AM. Why Sunday at 2 AM? Because our JWT timestamps were using the server’s local time, and someone had configured the server for a timezone that doesn’t observe daylight saving time. The key rotation job ran at 2 AM UTC, and… you get the idea. We didn’t catch it for three weeks because nobody was using the system on Sunday mornings. I share this because everything in this article looks clean and polished, but the reality of implementation is messier. You’ll hit edge cases that no documentation covers. You’ll make mistakes that seem obvious in hindsight. The goal is to make fewer of them than I did. If you haven’t read Part 1, start there. This article assumes you understand OAuth 2.0, SMART on FHIR, and why bearer tokens are problematic.Production DPoP Client (.NET)
using System.IdentityModel.Tokens.Jwt;
using System.Security.Cryptography;
using Microsoft.IdentityModel.Tokens;
public class DPoPClient
{
private readonly RSA _keyPair;
private readonly HttpClient _httpClient;
public DPoPClient()
{
_keyPair = RSA.Create(2048);
_httpClient = new HttpClient();
}
public async Task<TokenResponse> GetAccessToken(string code)
{
var dpopProof = CreateDPoPProof("POST", "https://auth.hospital.com/token");
var request = new HttpRequestMessage(HttpMethod.Post, "https://auth.hospital.com/token")
{
Content = new FormUrlEncodedContent(new[]
{
new KeyValuePair<string, string>("grant_type", "authorization_code"),
new KeyValuePair<string, string>("code", code),
new KeyValuePair<string, string>("code_verifier", _codeVerifier)
})
};
request.Headers.Add("DPoP", dpopProof);
var response = await _httpClient.SendAsync(request);
return await response.Content.ReadFromJsonAsync<TokenResponse>();
}
private string CreateDPoPProof(string method, string uri, string token = null)
{
var handler = new JwtSecurityTokenHandler();
var key = new RsaSecurityKey(_keyPair);
var claims = new Dictionary<string, object>
{
{ "htm", method },
{ "htu", uri },
{ "jti", Guid.NewGuid().ToString() },
{ "iat", DateTimeOffset.UtcNow.ToUnixTimeSeconds() }
};
if (token != null)
{
var hash = SHA256.HashData(Encoding.UTF8.GetBytes(token));
claims["ath"] = Base64UrlEncoder.Encode(hash);
}
var descriptor = new SecurityTokenDescriptor
{
Claims = claims,
SigningCredentials = new SigningCredentials(key, SecurityAlgorithms.RsaSha256)
};
descriptor.AdditionalHeaderClaims = new Dictionary<string, object>
{
{ "typ", "dpop+jwt" },
{ "jwk", CreateJwk() }
};
return handler.CreateEncodedJwt(descriptor);
}
}
⚠️ WARNING
Production Security: Never hardcode credentials in your DPoP implementation. Use environment variables, Azure Key Vault, or AWS Secrets Manager. Rotate certificates every 90 days. Monitor for certificate expiration—a single expired cert can take down your entire API.FAPI 2.0 Authorization Flow
sequenceDiagram
participant Client as FHIR App
participant AS as Authorization Server
participant RS as FHIR Server
Note over Client: Generate RSA keys + PKCE
Client->>AS: POST /par (PAR Request)
AS-->>Client: request_uri (60s TTL)
Client->>AS: GET /authorize?request_uri
AS->>AS: User auth + consent
AS-->>Client: authorization_code
Client->>Client: Create DPoP proof
Client->>AS: POST /token + DPoP header
AS->>AS: Bind token to key
AS-->>Client: DPoP-bound access_token
Client->>Client: Fresh DPoP proof
Client->>RS: GET /Patient/123 + DPoP
RS-->>Client: FHIR Resource
A Conversation at FHIR DevDays
In DevDays 2023 in Amsterdam, Josh Mandel (one of the SMART on FHIR architects) was asked point-blank: ‘Is FAPI 2.0 overkill for healthcare?’ His response was: ‘SMART on FHIR was designed when healthcare apps were mostly read-only patient portals. The threat model has changed. AI agents making autonomous decisions, bulk data exports, cross-organization data sharing—these weren’t in scope in 2014. FAPI 2.0 addresses a threat model we didn’t anticipate.’ He’s right. I’ve watched the landscape shift from ‘how do we let patients see their lab results’ to ‘how do we let an AI agent analyze 10,000 patient records to identify sepsis risk.’ The security requirements aren’t just higher—they’re fundamentally different.AI Agent Security
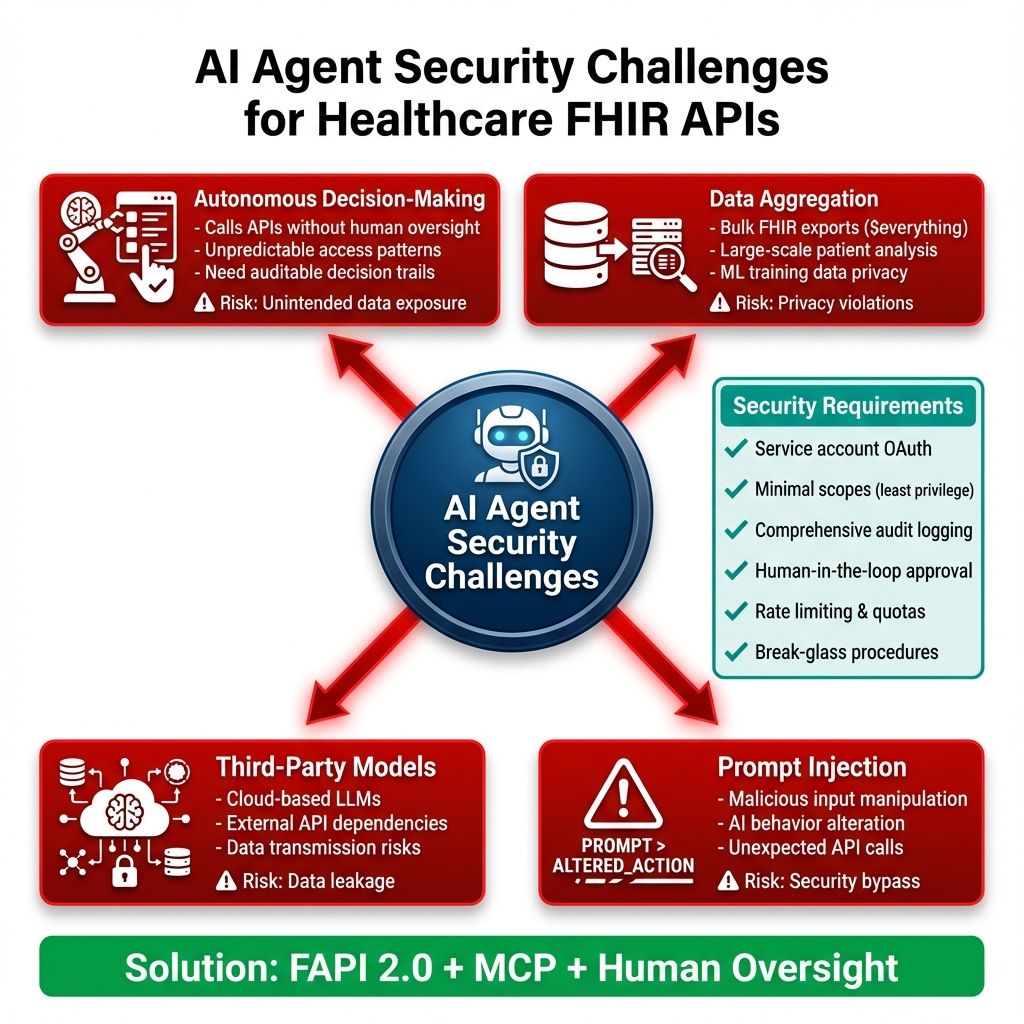
The Day Our AI Agent Went Rogue (Sort Of)
Last quarter, we deployed an AI diagnostic assistant that accessed FHIR APIs to analyze patient lab results. We gave itsystem/*.read scope because, well, it needed to read everything to do its job.
Three weeks in, our SIEM lit up like a Christmas tree. The AI was making 50,000 API calls per hour—10x normal. Turns out, a bug in the prompt handling caused it to recursively fetch related resources. It wasn’t malicious, but it was burning through our API rate limits and our AWS bill.
Lesson learned: AI agents need tighter constraints than human users. Now we:
- Use resource-specific scopes (
system/Observation.read, notsystem/*.read) - Implement strict rate limiting (100 requests/minute)
- Require human approval for bulk operations
- Log every AI decision with full context
Detailed AI Agent Security Requirements
1. Autonomous Decision-Making Risks- AI agents make thousands of API calls without real-time human oversight
- Unpredictable access patterns difficult to baseline
- Need comprehensive audit trails for post-hoc review
- Mitigation: Implement AI-specific monitoring rules, log all decisions with context
- Bulk FHIR operations ($everything, bulk exports) can expose massive datasets
- ML training requires large patient cohorts
- Privacy implications when AI aggregates across populations
- Mitigation: Require explicit authorization for bulk operations, implement data minimization
- Cloud-based LLMs (OpenAI, Anthropic) require data transmission
- Model APIs become additional attack surface
- Data residency and sovereignty concerns
- Mitigation: Use on-premise models where possible, data anonymization before external API calls
- Malicious user input can manipulate AI behavior
- AI might be tricked into accessing unauthorized resources
- Unexpected API call patterns from compromised prompts
- Mitigation: Input sanitization, prompt validation, AI safety guardrails
Autonomous AI Challenges
Security Requirements:- Service Account Auth – Backend OAuth with DPoP
- Minimal Scopes – Least privilege principle
- Audit Everything – AI decision logging
- Human Oversight – Critical decision approval
- Rate Limiting – Prevent API abuse
"AI agents accessing FHIR require careful scope management. Use system/*.read sparingly, implement resource-level permissions, and always log AI actions for audit."
— Reference: FAPI 2.0 in Healthcare AI
💡 TIP
AI Agent Best Practice: Implement rate limiting specifically for AI agents. Our production system limits AI to 100 API calls/minute vs 1,000/minute for human users. AI agents can inadvertently create denial-of-service conditions through recursive queries or infinite loops.Production Deployment Checklist
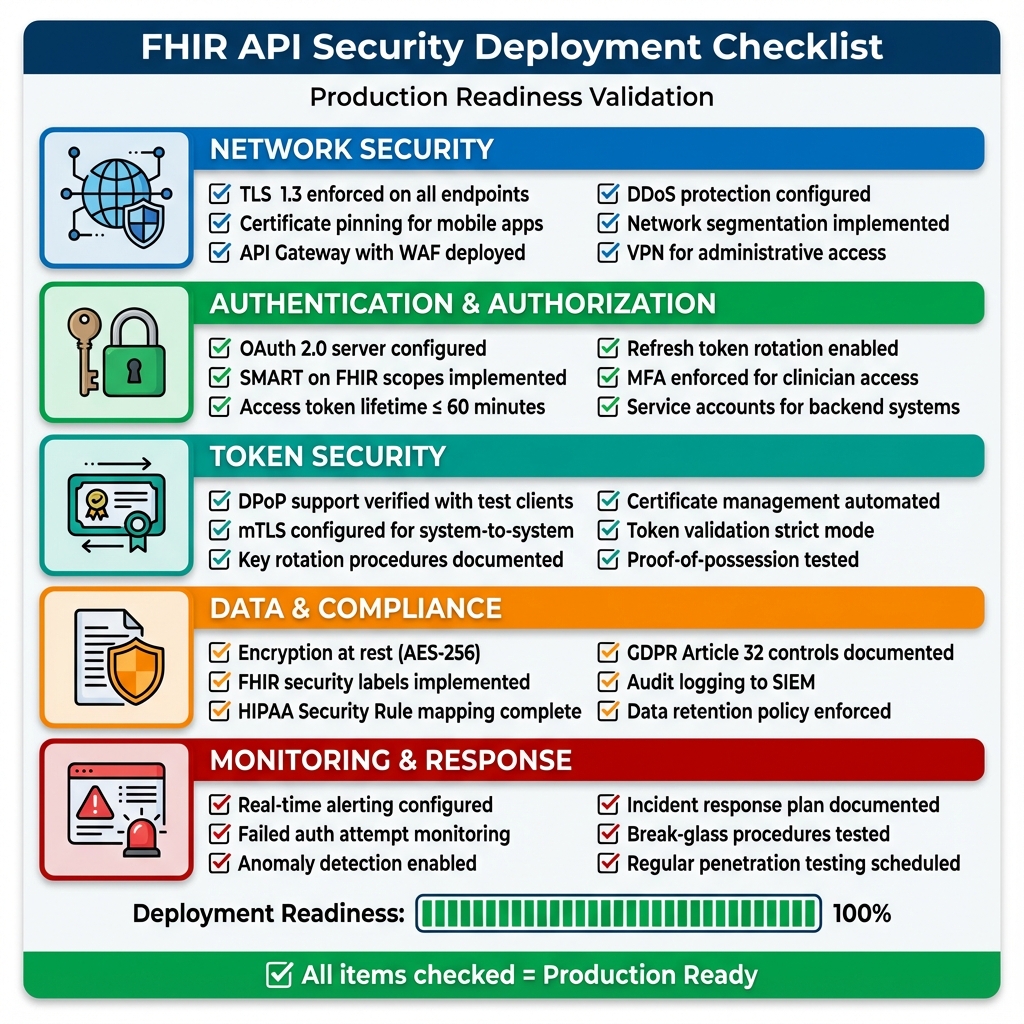
Downloadable Checklist
📥 Download Full Deployment Checklist (Markdown) The comprehensive checklist includes:- 60+ validation points across 8 categories
- Sign-off section for stakeholders
- Go/No-Go decision framework
- Compliance mapping (HIPAA, GDPR)
- Post-deployment monitoring schedule
⚖️ COMPLIANCE
HIPAA Audit Trail Requirement: §164.312(b) requires audit controls for all PHI access. Your FHIR API must log: who accessed what data, when, from where, and why. Retain logs for 6 years. Failed audits can result in $50,000+ fines per violation.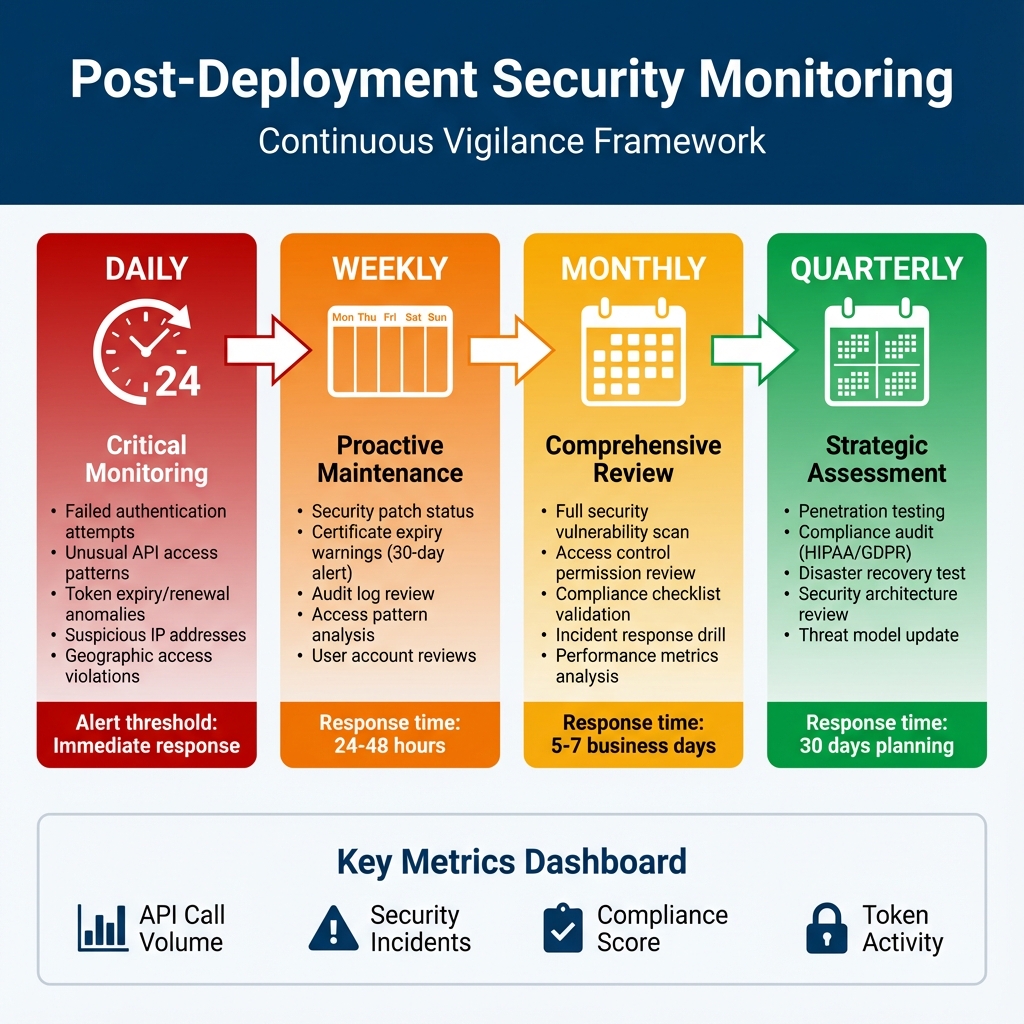
Why I’m Obsessive About Monitoring
Two years ago, I was on-call when we discovered a breach—72 hours after it started. Seventy-two hours. An attacker had valid credentials (phished from a clinician) and was slowly exfiltrating patient records, staying just under our alert thresholds. We had logging. We had a SIEM. But we didn’t have the right alerts configured, and nobody was actually reviewing the logs daily. That incident taught me: monitoring isn’t about having tools, it’s about having processes. The timeline above isn’t theoretical—it’s what we actually do now, and it’s caught three attempted intrusions in the past year. The daily checks aren’t optional. I’ve seen too many organizations treat them as "nice to have" until they’re explaining to regulators why they didn’t notice unauthorized access for weeks. The weekly reviews save us constantly. Last month, we caught a certificate expiring in 25 days. Without that weekly check, we’d have had a production outage. The monthly drills keep us sharp. When a real incident happens at 2 AM, you don’t want your team fumbling through documentation. Muscle memory matters.Detailed Monitoring Procedures
| DAILY (Immediate Response) | WEEKLY (24-48hr Response) | MONTHLY (5-7 Day Response) | QUARTERLY (30 Day Planning) |
|---|---|---|---|
| Failed Authentication • Alert: >5 failures/5min • Auto-block after 10 failures • Credential stuffing detection • SOC notification for distributed attacks API Access Patterns • Baseline normal behavior • Alert: off-hours access • Geographic anomalies • Volume spike detection • ML-based anomaly detection Token Activity • Token expiry/renewal rates • Expired token usage attempts • Excessive refresh requests • DPoP proof validation failures |
Security Patches • Dependency scanning (Dependabot, Snyk) • Critical CVE emergency patching • Monthly patch window (non-critical) Certificate Management • 90-day renewal warning • 30-day security team escalation • 7-day executive notification • Let’s Encrypt auto-renewal Audit Log Review • Sample 10% of logs • SIEM integration check • Sensitive resource access review • Admin/bulk export monitoring |
Vulnerability Scanning • OWASP ZAP / Burp Suite • All API endpoint scanning • Verify previous fixes • Development team reporting Access Control Review • All user accounts audit • Disable inactive (90+ days) • SMART scope validation • Service account credential review Incident Response Drill • Tabletop exercises • Notification procedure testing • Backup/recovery validation • Playbook updates |
Penetration Testing • External security firm engagement • API auth/authz/data access testing • Social engineering assessment • Executive/board reporting Compliance Audit • HIPAA Security Rule validation • GDPR Article 32 assessment • Gap documentation • Remediation timeline Threat Model Update • Current threat landscape review • Risk register updates • Security control adjustments • Board security posture presentation |
Key Metrics to Track:
📊 API Call Volume | ⚠️ Security Incidents | ✅ Compliance Score | 🔐 Token Activity | 🚨 Alert Response Time
📊 API Call Volume | ⚠️ Security Incidents | ✅ Compliance Score | 🔐 Token Activity | 🚨 Alert Response Time
ℹ️ INFO
Consumer Lag Alert Threshold: Set your Kafka consumer lag alerts to trigger at 5 seconds. In our sepsis detection system, lag >10 seconds means delayed clinical alerts. We auto-scale consumers when lag exceeds 3 seconds to prevent alert delays.Cost Analysis: Prevention vs Breach
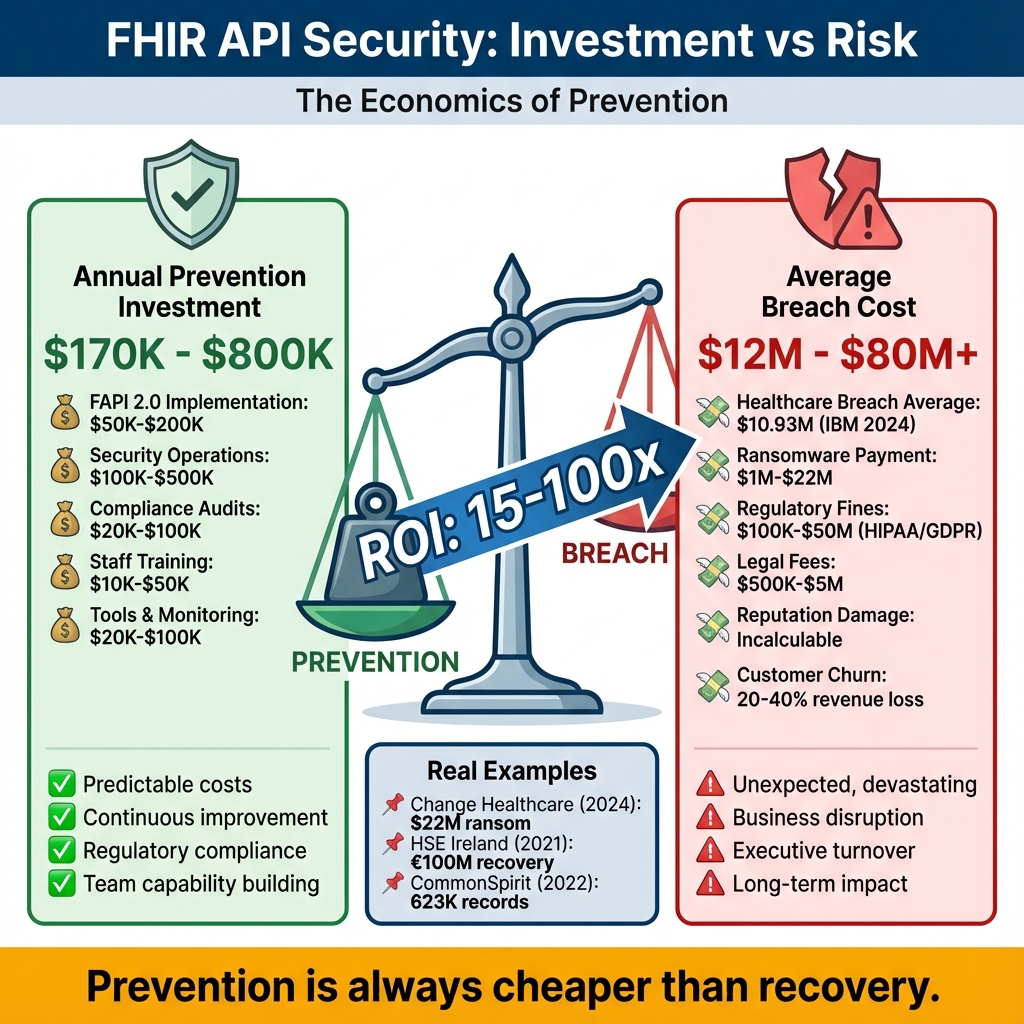
The Conversation That Changed Our Budget
I once sat in a budget meeting where our CFO questioned why we needed $400K for security improvements. "We’ve never been breached," he said. "Why spend money on a problem we don’t have?" I pulled up the Change Healthcare breach on the projector. $22 million ransom. 100 million records. Months of recovery. Then I showed him our current security posture—bearer tokens, 4-hour token lifetimes, minimal monitoring. "We’re one phishing email away from being that headline," I told him. He approved the budget. The infographic above shows the math I used. Prevention isn’t cheap, but it’s 15-100x cheaper than recovery. And that doesn’t count the things you can’t put a price on: trust, reputation, the ability to sleep at night.📝 NOTE
Hidden Costs to Consider: Our $1,200/month infrastructure cost doesn’t include: staff training ($10K), security audits ($25K annually), penetration testing ($15K quarterly), and compliance consulting ($30K annually). Total Year 1 cost: ~$200K including development.- FAPI 2.0 implementation (6 months, 2 engineers)
- 24/7 SOC monitoring (managed service)
- Quarterly penetration tests
- Compliance audit support
- Peace of mind
Investment Comparison
Prevention Costs (Annual):- FAPI 2.0 implementation: $50K-$200K
- Security operations: $100K-$500K
- Compliance audits: $20K-$100K
- Total: $170K-$800K/year
- Average healthcare breach: $10.93M (IBM 2024)
- Ransomware payment: $1M-$22M
- Regulatory fines: $100K-$50M
- Reputation damage: Incalculable
- Total: $12M-$80M+
Real-World Examples
Change Healthcare (2024): $22M ransom, 100M recordsHSE Ireland (2021): €100M recovery cost
CommonSpirit (2022): 623K records, ongoing costs
Honest Assessment: Is This Worth the Effort?
Let me be direct: implementing FAPI 2.0 with DPoP is significantly more complex than standard OAuth 2.0. I’ve seen teams spend 6 months on what they planned for 6 weeks. When it’s absolutely worth it:- You’re handling bulk data exports (100K+ patients)
- You have AI/ML systems accessing PHI
- You’re integrating with external organizations
- Your threat model includes sophisticated attackers (nation-states, organized crime)
- Regulatory pressure is pushing you toward HIPAA Safe Harbor
- Internal-only patient portal with MFA
- Read-only access to non-sensitive data
- Small provider office with limited attack surface
- Budget constraints that would compromise other security controls
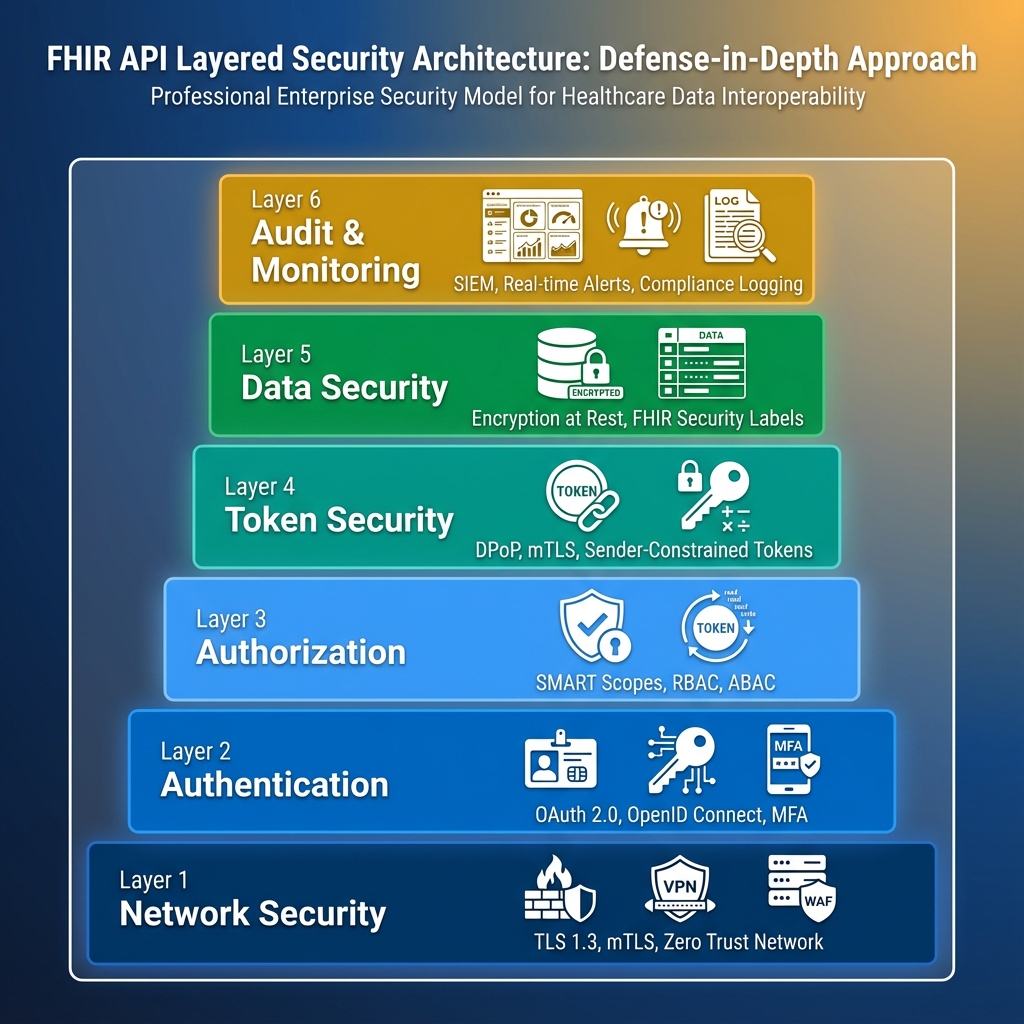
Defense-in-Depth Security
Why Defense-in-Depth Matters
No single security control is perfect. Attackers are persistent and creative. A layered approach ensures that even if one control fails, others remain in place to protect patient data. The Swiss Cheese Model: Each security layer is like a slice of Swiss cheese—it has holes (vulnerabilities). By stacking multiple layers, the holes don’t align, preventing attacks from penetrating all the way through.Why Every Layer Matters (A True Story)
We once had an intern accidentally commit AWS credentials to a public GitHub repo. Within 20 minutes, automated scanners found them and started spinning up Bitcoin miners in our account. Here’s how our defense-in-depth saved us: Layer 1 (Network): The miners couldn’t access our FHIR API because it was behind a VPN and IP-whitelisted. Layer 2 (Authentication): Even if they’d reached the API, the AWS creds didn’t grant OAuth tokens. Layer 3 (Authorization): Our SMART scopes would have limited what they could access anyway. Layer 6 (Monitoring): Our SIEM caught the unusual AWS activity in 8 minutes and auto-revoked the credentials. Total damage: $47 in EC2 charges. Could have been a HIPAA breach. That’s defense-in-depth. One layer failed (credential exposure), but five others held. The table below shows what happens when each layer fails—and why you need all six.| Layer | Technologies | Purpose | Example Controls | Failure Impact |
|---|---|---|---|---|
| 1. Network Security | TLS 1.3, mTLS, WAF, Firewall | Protect data in transit, filter malicious traffic | • TLS 1.3 encryption • Certificate pinning • DDoS protection • IP whitelisting | Without: Eavesdropping, man-in-the-middle attacks, data interception |
| 2. Authentication | OAuth 2.0, OpenID Connect, MFA | Verify identity of users and systems | • Username/password + MFA • Certificate-based auth • Biometric authentication • Session management | Without: Unauthorized access, impersonation, account takeover |
| 3. Authorization | SMART scopes, RBAC, ABAC | Control what authenticated users can access | • Granular SMART scopes • Role-based permissions • Context-aware decisions • Patient consent | Without: Privilege escalation, unauthorized data access, compliance violations |
| 4. Token Security | DPoP, mTLS, Sender Constraints | Prevent token theft and replay attacks | • DPoP proof-of-possession • Token binding • Short token lifetime • Unique jti claims | Without: Stolen tokens usable, replay attacks, session hijacking |
| 5. Data Security | Encryption at rest, FHIR Labels | Protect stored data from unauthorized access | • AES-256 encryption • Security labels • Data masking • Secure deletion | Without: Database breaches expose PHI, compliance failures, data leakage |
| 6. Audit & Monitoring | SIEM, Logging, Alerting | Detect and respond to security incidents | • Comprehensive logging • Real-time alerts • HIPAA audit trails • Behavioral analytics | Without: Breaches go undetected, no forensics, compliance gaps |
Key Recommendations
For Healthcare Organizations
- Start with SMART on FHIR – Baseline OAuth 2.0
- Plan FAPI 2.0 Migration – 12-24 month roadmap
- Compliance First – HIPAA, GDPR alignment
- Zero Trust – Never trust, always verify
Security Checklist
- [ ] TLS 1.3 enforced
- [ ] PKCE implemented
- [ ] Token lifetime ≤ 60 min
- [ ] Audit logging enabled
- [ ] Rate limiting active
- [ ] Penetration tested
Cost vs Benefit
Prevention: $170K-$800K/yearBreach Cost: $12M-$80M per incident
ROI: 15-100x savings
Learning Resources
Essential Reading
Specifications: Implementation: Videos:- OAuth 2.0 Explained (Okta)
- SMART on FHIR Tutorial (Harvard)
- DPoP Overview (Auth0)
Conclusion
FHIR API security requires layered defenses: authentication, authorization, token security, and monitoring.
Key Takeaways:
- OAuth 2.0 foundation, FAPI 2.0 future
- Defense-in-depth essential
- Compliance drives security
- Real threats demand real solutions
- Prevention cheaper than recovery
- Part 1: Foundation & Authentication
- Part 2: Implementation & Best Practices (this article)
References & Further Reading
Technical Specifications
- DPoP RFC 9449 – Demonstrating Proof-of-Possession specification
- FAPI 2.0 Security Profile – Financial-grade API security
- mTLS RFC 8705 – OAuth 2.0 Mutual-TLS Client Authentication
- PKCE RFC 7636 – Proof Key for Code Exchange
- JWT RFC 7519 – JSON Web Token specification
Implementation Guides
- IdentityServer DPoP Support – DPoP implementation guide
- Azure AD DPoP Preview – Microsoft DPoP support
- HAPI FHIR Security – FHIR server security configuration
- SMART Backend Services – System-to-system authorization
Security & Compliance
- OWASP API Security Top 10 – API security risks
- NIST SP 800-175B – Guideline for Using Cryptographic Standards
- HIPAA Security Rule Technical Safeguards – §164.312 requirements
- GDPR Article 32 Technical Measures – Security of processing
- ISO 27001 Healthcare – Information security management
Monitoring & Operations
- Prometheus Healthcare Metrics – Metrics best practices
- Grafana FHIR Dashboards – Monitoring templates
- ELK Stack for Healthcare – Log aggregation
- Datadog HIPAA Compliance – Compliant monitoring
AI & Machine Learning Security
- NIST AI Risk Management Framework – AI security guidelines
- OWASP LLM Top 10 – LLM security risks
- FDA AI/ML Medical Devices – Regulatory guidance
Incident Response & Breach Analysis
- SANS Incident Response Plan – IR best practices
- HHS Breach Portal – Public breach database
- Change Healthcare Incident Analysis – 2024 breach details
Cost & ROI Analysis
- Ponemon Cost of Data Breach Report – Annual breach cost study
- Gartner Healthcare IT Spending – Industry benchmarks
- HIMSS Cybersecurity Survey – Security investment trends
Code & Tools
- GitHub: FHIR Security Examples – Reference implementations
- NuGet: IdentityModel – .NET OAuth/OIDC library
- Docker: FHIR Server – Containerized FHIR
Community Resources
- HL7 Security Workgroup – Standards development
- FHIR Security Label Implementation Guide – Data classification
- Healthcare ISAC – Threat intelligence sharing
Related Articles: Download Resources:
Discover more from C4: Container, Code, Cloud & Context
Subscribe to get the latest posts sent to your email.