Executive Summary
Part 1 of 2: Foundation & Authentication
🏥
HEALTHCARE INTEROPERABILITY SERIES
This article is part of a comprehensive series on healthcare data standards and interoperability.
- HL7 v2: The Messaging Standard That Powers Healthcare IT
- Building GDPR-Compliant FHIR APIs: A European Healthcare …
- EMR Modernization: Migrating from Legacy HL7 v2 to FHIR
- HL7 v3: Understanding RIM and Why v3 Failed to Replace v2
- FHIR Subscriptions: Building Real-Time Event-Driven Healt…
- ePrescribing in EU and Ireland: FHIR-Based Electronic Pre…
- FHIR Integration Best Practices: Lessons from Production
- FHIR API Security Part 1: Foundation & Authentication (this article)
- FHIR API Security Part 2: Implementation & Best Prac…
- Real-Time Healthcare Data Pipelines: Kafka + FHIR for Cli…
- Building Interoperable Healthcare Data Systems for AI: A …
- Case Study: Building a Modern FHIR Patient Timeline Explo…
- Real-world FHIR security threats (2025)
- SMART on FHIR authentication flow
- OAuth 2.0 vulnerabilities
- Why FAPI 2.0 is essential for healthcare
- Token security fundamentals
Why I’m Writing This
Last year, I watched a healthcare organization scramble after their FHIR API was compromised. The breach? A stolen OAuth bearer token that gave attackers unfettered access to patient records for three days before anyone noticed. The cost? $4.2 million in remediation, regulatory fines, and a damaged reputation that took months to rebuild. That incident could have been prevented with sender-constrained tokens—the kind FAPI 2.0 mandates. But here’s the thing: most healthcare organizations I’ve worked with are still running OAuth 2.0 with bearer tokens, blissfully unaware they’re one stolen token away from a catastrophe. This two-part series is my attempt to change that. Not with academic theory, but with practical, battle-tested guidance drawn from years of implementing FHIR security in production environments.The FHIR Security Threat Landscape (2025)
Real-World Attacks on Healthcare APIs
Recent Incidents (2023-2025):-
Change Healthcare Ransomware Attack (Feb 2024)
- 100+ million patient records compromised
- API credentials stolen via phishing
- $22 million ransom paid
- Lesson: API keys alone are insufficient
-
CommonSpirit Health Data Breach (Oct 2022)
- 623,000 patient records exposed
- Unpatched FHIR API vulnerability
- Lesson: Regular security audits critical
-
Irish HSE Ransomware (May 2021)
- National healthcare system paralyzed
- Legacy API authentication bypassed
- €100 million recovery cost
- Lesson: Zero-trust architecture essential
OWASP API Security Top 10 (2023)
| OWASP Risk | FHIR-Specific Example | Mitigation |
|---|---|---|
| API1: Broken Object Level Authorization | Accessing Patient/123 when authorized for Patient/456 | Resource-level scopes |
| API2: Broken Authentication | Weak OAuth client secrets, no MFA | FAPI 2.0, DPoP |
| API3: Broken Property Authorization | Reading SSN without consent | Element-level security |
| API4: Unrestricted Resource Access | No rate limiting | Throttling, quotas |
| API5: Broken Function Authorization | Non-admin calling $export | SMART scopes |
SMART on FHIR Authentication
What is SMART on FHIR?
SMART (Substitutable Medical Applications, Reusable Technologies) enables third-party apps to securely access FHIR servers using OAuth 2.0. Key Components:- Launch Contexts: EHR launch vs standalone launch
- Scopes:
user/Patient.read,patient/*.write,system/*.read - Context Parameters: patient, encounter, location, practitioner
sequenceDiagram
participant EHR as EHR System
participant App as SMART App
participant AS as Auth Server
participant FHIR as FHIR Server
EHR->>App: 1. Launch (iss + launch token)
App->>FHIR: 2. GET /.well-known/smart-configuration
FHIR-->>App: OAuth endpoints
App->>AS: 3. Authorization request
(scopes, launch context)
AS->>AS: 4. User authenticates & consents
AS-->>App: 5. Authorization code
App->>AS: 6. Token request (code)
AS-->>App: 7. Access token + patient context
App->>FHIR: 8. API request (Bearer token)
FHIR-->>App: FHIR resources
ℹ️ INFO
Real Cost of Breaches: The average healthcare data breach costs $10.93 million (Ponemon Institute, 2024). Change Healthcare’s 2024 ransomware attack cost $22 million in ransom alone, plus months of recovery. HSE Ireland spent over €100 million recovering from their 2021 attack.OAuth 2.0 vs FAPI 2.0
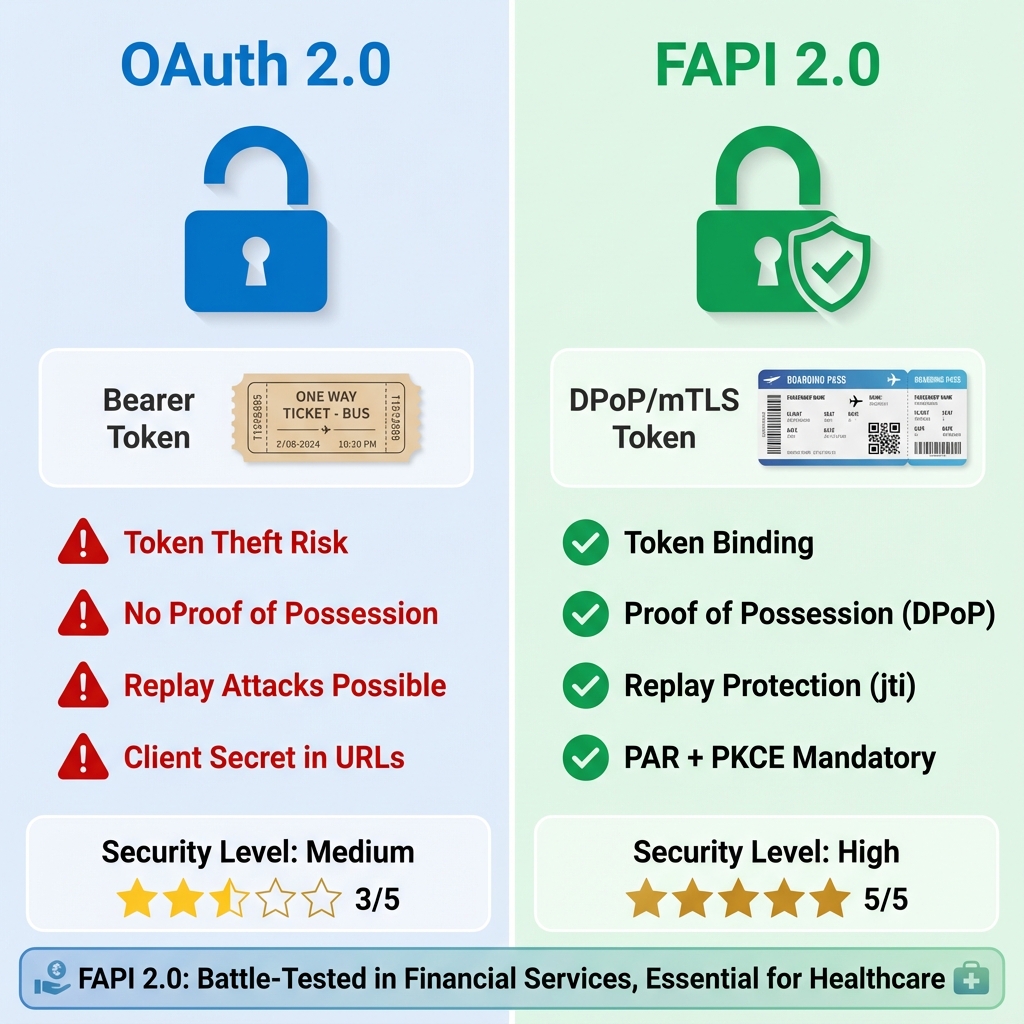
The Bearer Token Problem (And Why It Matters)
Let me tell you about bearer tokens. They’re called "bearer" because whoever bears (holds) the token can use it. It’s like cash—if someone steals your $100 bill, they can spend it. No questions asked. I once explained this to a hospital CISO using an analogy that stuck: "Your OAuth bearer token is like leaving your hospital badge on a coffee shop table. Anyone who picks it up can walk into your facility." His response? "We’d never do that with physical badges." Exactly. So why do we do it with API tokens? This is where FAPI 2.0 comes in. Instead of bearer tokens (cash), it uses sender-constrained tokens (credit cards). Even if someone steals your credit card number, they can’t use it without additional verification. In FAPI 2.0’s case, that verification is cryptographic proof that you possess the private key associated with the token. The bus ticket vs airline ticket analogy (credit to Hamid Jahanzad) captures this perfectly:- OAuth 2.0 bearer token = Bus ticket. Anyone holding it can board.
- FAPI 2.0 DPoP token = Airline ticket. Requires ID verification at the gate.
Expert Insights & Industry Quotes
Why FAPI 2.0 Matters for Healthcare
"Healthcare APIs handle the most sensitive data imaginable—patient medical records, diagnostic results, genetic information. The OAuth 2.0 bearer token model, while revolutionary in 2012, is insufficient for today’s threat landscape. FAPI 2.0’s sender-constrained tokens represent a paradigm shift: stolen tokens become useless without the cryptographic proof that only the legitimate client possesses." — Travis Spencer, CEO, Curity (OAuth Security Expert)
"In financial services, we learned that bearer tokens are like cash—whoever holds them can spend them. FAPI 2.0’s DPoP and mTLS ensure tokens work like credit cards: bound to the rightful owner and requiring verification at point of use." — OpenID Foundation FAPI Working Group
"The future of healthcare AI depends on secure, standardized protocols for context sharing. MCP with OAuth 2.0/FAPI 2.0 provides that foundation—AI agents can access necessary patient data while maintaining strict security boundaries." — Reference: Hamid Jahanzad on FAPI 2.0 in Healthcare AI
Key Security Features Summary
SMART on FHIR Key Features
✅ Standardized App Launch – Consistent authorization across all EHR vendors✅ Granular Scopes – Fine-grained permissions (patient/.read, user/Observation.write)
✅ Context Awareness – Automatic patient/encounter context propagation
✅ OpenID Connect Integration – User identity alongside authorization
✅ Backend Services – System-to-system authentication for bulk operations
FAPI 2.0 Security Enhancements
✅ Sender-Constrained Tokens – DPoP or mTLS binding prevents token theft✅ PAR (Pushed Authorization) – Server-to-server parameter exchange
✅ PKCE Mandatory – Protection even for confidential clients
✅ Short Token Lifetime – 15-60 minute maximum validity
✅ Strong Client Auth – private_key_jwt or certificate-based
✅ Replay Protection – Unique jti (JWT ID) in each proof
⚖️ COMPLIANCE
ONC Certification Requirement: The 21st Century Cures Act requires SMART on FHIR support for EHR certification. If you’re building a patient-facing app or provider portal, SMART authorization is mandatory for ONC compliance. FAPI 2.0 is recommended but not yet required.Implementation Recommendations
For Healthcare Organizations
1. Start with SMART on FHIR- Implement basic OAuth 2.0 + SMART scopes first
- Use established authorization servers (Azure AD, Auth0, IdentityServer)
- Test with public SMART sandbox environments
- Assess current token security (bearer vs sender-constrained)
- Implement DPoP support incrementally
- Consider mTLS for backend services
- Set roadmap: OAuth 2.0 (2024) → FAPI 2.0 (2025-2026)
- Map security controls to HIPAA Security Rule
- Document GDPR Article 32 compliance
- Implement audit logging (NIST 800-53 AU family)
- Regular penetration testing
- Never trust, always verify—even internal APIs
- Implement network segmentation
- Use API gateways with WAF capabilities
- Monitor API traffic with SIEM integration
For API Developers
1. Use Established Libraries- IdentityServer/Duende (FAPI 2.0 certified)
- HAPI FHIR (comprehensive SMART support)
- Azure Healthcare APIs (managed FHIR + OAuth)
- [ ] TLS 1.3 enforced on all endpoints
- [ ] PKCE implemented for all OAuth flows
- [ ] Access tokens expire within 60 minutes
- [ ] Refresh token rotation enabled
- [ ] Rate limiting on all API endpoints
- [ ] Input validation on all parameters
- [ ] Audit logging for all data access
- Unit tests for authorization logic
- Integration tests with SMART sandbox
- Security testing with OWASP ZAP
- Compliance validation with Inferno suite
The Future of FHIR Security (2025-2030)
Emerging Trends
1. AI Agent Authorization- OAuth 2.0 extensions for autonomous AI systems
- Model Context Protocol (MCP) + FAPI 2.0 integration
- Granular AI-specific scopes (e.g.,
ai/diagnostics.read) - Human-in-the-loop approval for critical decisions
- NIST post-quantum algorithm adoption (2025-2027)
- Migration from RSA to lattice-based signatures
- DPoP evolution to support quantum-safe keys
- Self-sovereign identity (SSI) for patient control
- Verifiable credentials for healthcare professionals
- Blockchain-based audit trails
- Prove data attributes without revealing actual data
- Privacy-preserving clinical research
- GDPR compliance by design
- Policy-as-code with Open Policy Agent (OPA)
- Automated security testing in CI/CD
- Infrastructure-as-code for API gateways
Industry Predictions
By 2026:- 50% of new FHIR implementations will use FAPI 2.0
- DPoP becomes default for healthcare APIs
- AI agents accessing FHIR standardized
- OAuth 2.0 bearer tokens deprecated in healthcare
- Quantum-resistant algorithms required by regulation
- Cross-border EU FHIR exchange fully operational
- Patient-controlled decentralized health records
- Zero-knowledge proofs for clinical trials
- AI-driven real-time threat detection standard
Real Talk: Where to Start
I get asked this constantly: "We’re overwhelmed. Where do we even begin?" Here’s what I tell teams based on what’s actually worked in production: If you’re starting from scratch:- Don’t reinvent the wheel. Use Azure AD, Auth0, or IdentityServer. They handle the OAuth complexity.
- Implement SMART on FHIR scopes from day one. Retrofitting authorization is painful.
- Start with short token lifetimes (15 minutes). You can always extend them; shortening them later breaks clients.
- Don’t panic and rip everything out. FAPI 2.0 is evolutionary, not revolutionary.
- Start with a roadmap: Q1 2025 – Assessment, Q2-Q3 – DPoP implementation, Q4 – Migration.
- Run both systems in parallel during migration. Your users will thank you.
- Map your current controls to HIPAA Security Rule and GDPR Article 32. You’re probably closer than you think.
- Document everything. Compliance is 50% doing the right thing, 50% proving you did it.
- Automate audit logging. Manual log reviews don’t scale and auditors know it.
📝 NOTE
Implementation Timeline: Based on our experience, expect 3-6 months for FAPI 2.0 implementation: Month 1-2 (Assessment & Planning), Month 3-4 (DPoP/mTLS Implementation), Month 5-6 (Testing & Migration). Budget 2 FTE engineers plus security review time.Conclusion: Building Secure Healthcare APIs
FHIR API security is not a destination—it’s a continuous journey. As threats evolve, so must our defenses.
Key Takeaways
-
OAuth 2.0 is Foundation, FAPI 2.0 is Future
- Start with SMART on FHIR today
- Plan migration to FAPI 2.0 within 12-24 months
-
Defense-in-Depth is Essential
- No single security control is sufficient
- Layer network, authentication, authorization, token security
-
Compliance Drives Security
- HIPAA and GDPR requirements align with best practices
- Security audits reveal vulnerabilities before attackers do
-
Real-World Threats are Real
- Change Healthcare, HSE Ireland breaches prove the stakes
- $22M ransoms and €100M recovery costs are preventable
-
The Future is AI + Zero Trust
- Prepare for AI agents accessing FHIR
- Quantum-resistant cryptography coming by 2027
Final Recommendation
"Don’t wait for a breach to prioritize security. Implement SMART on FHIR authentication, plan your FAPI 2.0 roadmap, and build defense-in-depth from day one. The cost of prevention is always less than the cost of recovery."Continue to Part 2: Implementation & Best Practices for production code, architecture patterns, and comprehensive resources.
Continue to Part 2
Part 2 covers:
- Complete DPoP implementation (.NET code)
- FAPI 2.0 authorization flow (Mermaid diagram)
- Defense-in-depth security architecture
- AI agent security patterns
- 50+ learning resources
- Comprehensive standards references
References & Further Reading
Official Specifications & Standards
- HL7 FHIR R4 Specification – Official FHIR R4 documentation
- SMART App Launch Framework – SMART on FHIR authorization specification
- FAPI 2.0 Security Profile – Financial-grade API security
- OAuth 2.0 RFC 6749 – OAuth 2.0 authorization framework
- OpenID Connect Core 1.0 – Identity layer on OAuth 2.0
- DPoP RFC 9449 – Demonstrating Proof-of-Possession
Healthcare Regulations & Compliance
- ONC 21st Century Cures Act – US interoperability requirements
- HIPAA Security Rule – Healthcare data protection standards
- GDPR Article 32 – Security of processing (EU)
- NIST Cybersecurity Framework – Security best practices
Industry Reports & Breach Analysis
- Change Healthcare Breach Report (2024) – $22M ransomware attack
- HSE Ireland Ransomware Analysis – €100M+ recovery cost
- Verizon 2024 Data Breach Investigations Report – Healthcare breach trends
- Ponemon Institute Healthcare Data Breach Study – Average breach cost: $10.93M
Implementation Guides & Tools
- Microsoft FHIR Server – Open-source FHIR server (.NET)
- HAPI FHIR – Java-based FHIR implementation
- IdentityServer Documentation – OAuth 2.0/OIDC server
- Azure AD B2C FHIR Integration – Cloud FHIR services
- SMART Health IT Sandbox – Test SMART apps
- Inferno Testing Tool – ONC certification testing
Security Research & Best Practices
- OWASP API Security Top 10 – API security risks
- OAuth 2.0 Security Best Practices – Current best practices
- NIST SP 800-63B – Digital identity guidelines
- CIS Controls for Healthcare – Security control framework
Community & Learning Resources
- HL7 FHIR Chat – Community support
- FHIR DevDays – Annual FHIR conference
- Health Samurai FHIR School – Free FHIR training
- Grahame Grieve’s Blog – FHIR co-creator insights
Continue to Part 2: FHIR API Security Part 2: Implementation & Best Practices Learn about DPoP implementation, AI agent security, production deployment checklists, and real-world monitoring strategies.
Discover more from C4: Container, Code, Cloud & Context
Subscribe to get the latest posts sent to your email.